My Modern Workforce is scattered and no longer in a central location; how do I manage their devices and applications?
I believe that the pandemic we are all experiencing has hastened the permanent adoption of a lot of ideas that people and companies were experimenting with pre-pandemic, virtual classrooms, grocery delivery, and remotely working. Pre-pandemic IT Teams were slowly kicking the tires on moving some of their company’s server infrastructure over to the cloud. Now they are not only moving their company’s entire server infrastructure over to the cloud but now they are contemplating moving their whole Modern Workforce over to Windows Virtual Desktops. IT Teams are also struggling to manage all of the end-users company devices or company applications utilized on end-user personal devices. In the last two blogs, we talked a lot about security and how transitioning from Office 365 to Microsoft 365 will provide you several new features to secure your company’s data and server infrastructure. This blog, we will still talk about a little security but also the management of an end-user company-issued or personal device.
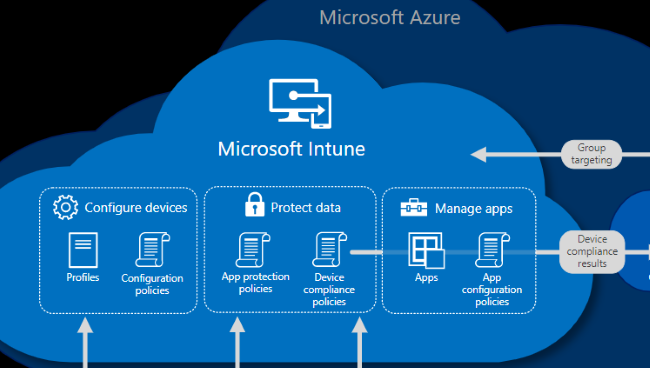
Microsoft Intune is included in your company’s Microsoft 365 subscription and consolidates mobile device management (MDM) and mobile application management (MAM) into one console. Your IT team controls how your company’s end-user devices are used, including mobile phones, tablets, and laptops. The team can configure policies to deploy, configure, and secure apps, all the while managing the end-user experience. On personal devices or BYOD, Microsoft Intune helps make sure your company data stays protected and can isolate company data from personal data.
Manage Devices
In Microsoft Intune, your IT team manage devices using an approach that’s right for your company. The team should have full control of any company device, including settings, features, and security. In this approach, devices and end-users of these devices “enroll” in Intune. Once enrolled, they will receive the rules and settings through policies configured in Microsoft Intune. For instance, the default policies can set password and PIN requirements, create a VPN connection, set up threat protection, and more.
Personal devices or bring-your-own devices (BYOD), end-users may not want the IT team to have full control. With this approach, the policies can give users options. In this case, end-users can enroll their devices if they want full access to company resources. Or, if these end-users only want access to email or Microsoft Teams, then use app protection policies that require multi-factor authentication (MFA) to use these apps.
When devices are enrolled and managed in Microsoft Intune, your IT team can ensure that either company devices or personal devices meet the company’s security and compliance standards; jailbroken devices should be blocked. Your IT teams can push certificates to devices so end-users can easily access the company Wi-Fi network or use a VPN to connect to the company’s network. Regularly run reports to identify out of compliance end-user devices will give insights to the IT team of which devices need remediation to bring them back into the set compliance standards. Most importantly, your IT team can remove company data if a device is lost, stolen, or not used anymore.
Manage apps
Mobile application management (MAM) in Microsoft Intune protects company data at the application level, including custom apps and store apps. Microsoft Intune will deploy and manage these apps on the company and personal devices, according to the end-user or device assigned groups. This feature enables end-users in your company to be productive on all of their devices. Your IT team can configure these apps to start or run with specific settings enabled and update existing apps already on devices. Senior-level IT managers can run reports that track the usage of custom apps to help determine the adoption level by the end-users. When the IT team repurposes a device, they can do a selective wipe by removing only company data from apps and redeploy the device. In conjunction with managing apps, your IT team can secure app more granular using app protection policies.
App protection policies use Azure AD identity to isolate company apps to only access company data, and other apps only access end-user personal data. In this way, your IT team has control of company data, while end-users maintain control and privacy over their personal data. The team should also deploy an additional app protection policy to prevent data from crossing the company/personal data boarder. An app protection policy designed to secure access on personal devices by restricting actions end-users can take, such as copy-and-paste, save, and view.
Device and App management is one of the essential functions, if not, the essential function of today’s Modern IT teams. The Modern Workforce still has to be productive, and when they can’t access company data and apps, that hinders said productivity. The IT team has to have the right tools to get end-users back to work, and when they have multiple tools to manage one device, it takes longer for that team to get that end-user back to work. Microsoft Intune helps solve that problem by providing one console to manage company or BYOD devices along with the apps needed for end-users to be productive. That’s why this is reason number 3 for your company to transition its Office 365 licenses to Microsoft 365. Microsoft Intune is one of the newest features for your IT team to take advantage of when managing devices and apps. Next week I will outline a little bit of what Big Green IT brings to your transition by providing a unique support experience. Until then, stay green.
Click here for more information on Intune

Recent Posts
- Unlocking Efficiency with Copilot for Microsoft 365: Top Things to Try
- Effortlessly Integrated: Copilot for Microsoft 365 and your IT Ecosystem
- Driving Seamless User Adoption: Empowering Teams with Copilot for Microsoft 365
- Maximizing Cost-Effectiveness with Copilot for Microsoft 365: A Strategic Approach for CIOs and VPs of IT
- Maximizing Efficiency with Copilot for Microsoft 365: Top 10 Prompts to Enhance Your Workflow
